The Security Hardening section in ADSelfService Plus provides a centralized console for administrators to manage security settings for configured features. These settings help protect the application from potential vulnerabilities by enforcing secure communication protocols, encrypting sensitive data, and applying critical hardening mechanisms. The Security Score offers a quantifiable assessment of the product's security status, based on your enabled security settings.
To configure the security settings of ADSelfService Plus:
| Enable HTTPS for Product | Ensure secure communication between clients and ADSelfService Plus. |
| Enable Secure TLS Version | Ensure that secure TLS versions, such as TLSv 1.2, are enabled to maintain strong encryption standards. |
| Enable Secure Cipher Suites | Ensure only secure TLSv1.2 cipher suites are enabled for HTTPS to enhance security. Refer to the security deployment guidelines for a detailed overview. |
| Configure Password Encryption for SSL Keystore | Encrypt the password used to access the SSL keystore.
(or) To strengthen security, encrypt the keystore password to protect certificate data, as storing it in plain text increases the risk of exposure. |
Note: For more details on the above configurations, refer to the Connection settings page
| Change the Default Admin Password | Change the default ADSelfService Plus admin account password to a stronger, more secure one to enhance security and protect accounts from unauthorized access. |
| Enable LDAP SSL | Ensure secure communication between Active Directory and ADSelfService Plus by enabling this option. |
| Hide Employee Search/Organization Chart From Login Page | Restrict the visibility of employee information to unauthenticated users on the login page. This helps minimize the exposure of organizational data. Refer to this page for more details on this setting. |
| Enable TLS/SSL for Mail Server | Ensure secure communication between ADSelfService Plus and the mail server using TLS/SSL. |
| Enable SSL Pinning for Mobile App | Prevent man-in-the-middle attacks in the ADSelfService Plus mobile app by revalidating the SSL certificate after the SSL handshake. Check this page for more details. |
| Change Password for Database Backups | Protect ADSelfService Plus database backup files with a strong, secure password. |
| Restrict User Access to Agent If SSL Certificate Is Invalid | Prevent users from going through the MFA process and performing self-service actions from the login screen if the SSL certificate applied in the product becomes invalid. For more information, refer to this page. |
| Register for Security Updates | Configure this option to receive timely alerts and notifications regarding product security patches and updates by providing your subscription details in the prompt that appears. Learn more. |
Note: Unconfigured features are excluded from the Security Score calculation.
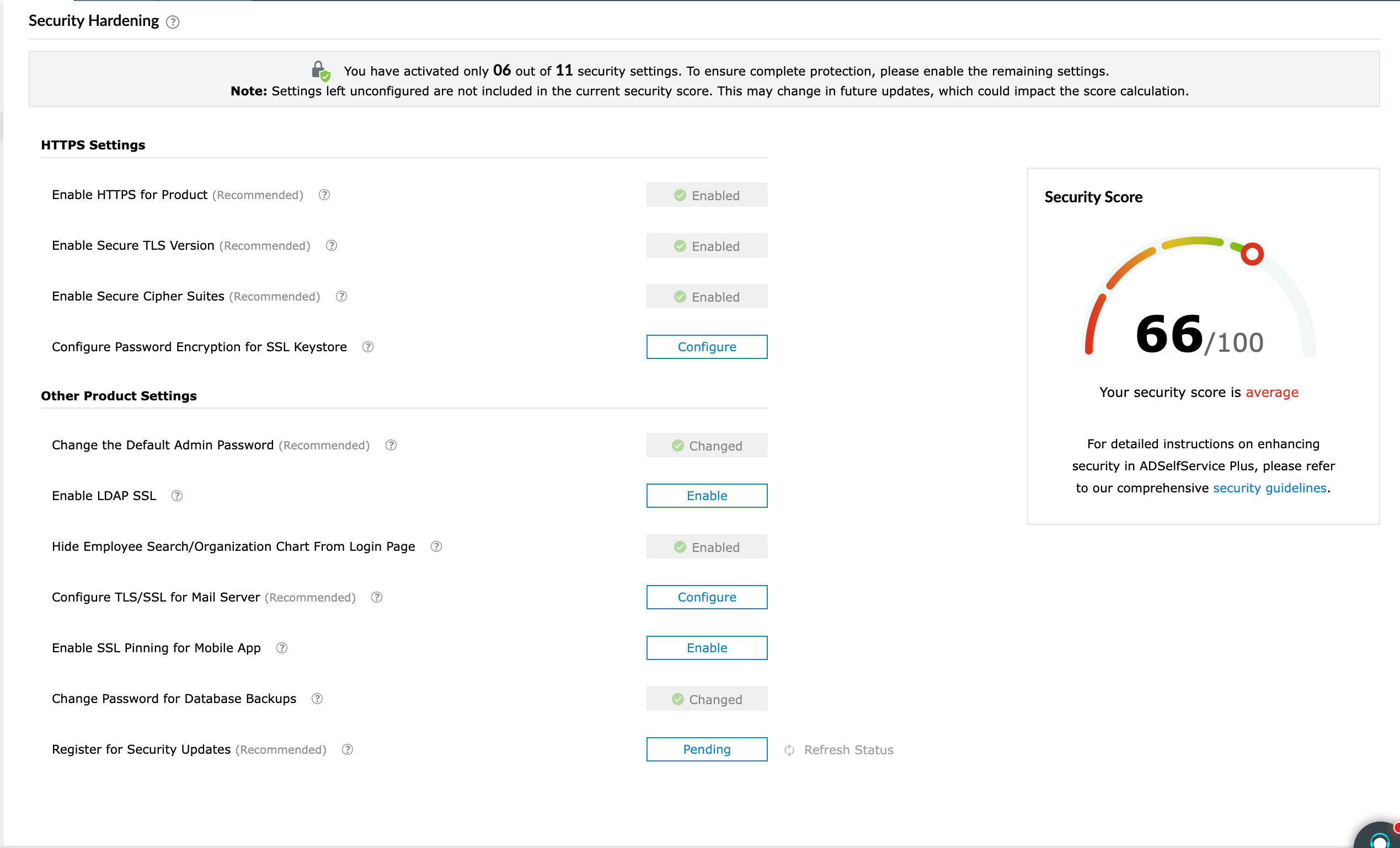
Fig. 1: Configure the Security Hardening settings to enhance the overall security posture of ADSelfService Plus.
To keep your ADSelfService Plus instance secure, our security team will use the registered contact details to notify you of important security updates. You can register the contact information of your operations or security team to receive timely updates from ManageEngine.
To ensure uninterrupted delivery, registered email addresses must be re-verified every 365 days. The information provided will be used only for sending security updates. A verification link will be sent to the registered email address, which must be confirmed within 7 days; otherwise, you will not receive updates.
All critical and high-risk vulnerabilities that have been fixed will be communicated to you once the issue is resolved in the product. Updates will be sent to both primary and secondary registered email addresses, which are treated as separate entities. Notifications will cover vulnerabilities identified and addressed, whether internal or external.
Previously, these updates were sent only to licensed email addresses. Going forward, updates will also be sent to the registered email addresses. Critical vulnerabilities are resolved within 24 hours of identification, while highly critical vulnerabilities are typically resolved within 10 days. You will be notified once each issue is fixed.
In certain cases, proactive measures designed to prevent potential public vulnerabilities will also be communicated to registered email addresses.
Copyright © 2025, ZOHO Corp. All Rights Reserved.