How to enable MFA for VPN logins and RADIUS-supported endpoint logins
Note: MFA for VPN logins requires the Professional edition of ADSelfService Plus with Endpoint MFA.
ADSelfService Plus' Endpoint MFA adds an extra step of authentication for VPN and endpoint logins that use RADIUS authentication (like Microsoft Remote Desktop Gateway and VMware Horizon) for enhanced security.
ADSelfService Plus requires the usage of a Windows Network Policy Server (NPS) on the VPNs and endpoints. It comes bundled with an NPS extension, which should be installed on the NPS. This extension facilitates communication between the NPS and ADSelfService Plus for MFA during VPN and endpoint logins.
How it works:
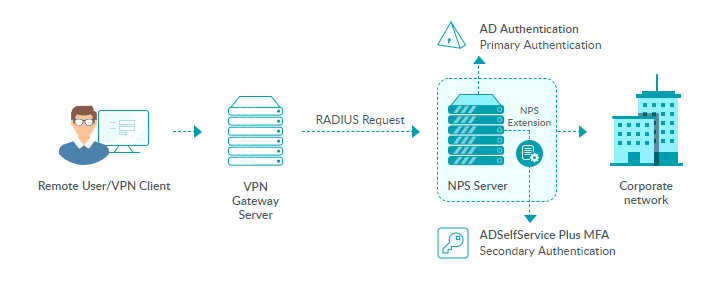
Once the VPN or endpoint server is configured to use RADIUS authentication, and the NPS extension is installed on the RADIUS server, here is how the authentication process works:
- A user tries to establish a connection by providing their username and password to the VPN or endpoint server.
- The server converts the request to a RADIUS Access-Request message and sends it to the NPS where the ADSelfService Plus’ NPS extension is installed.
- If the username and password combination is correct, the NPS extension triggers a request for secondary authentication with the ADSelfService Plus server.
- ADSelfService Plus performs the secondary authentication and sends the result to the NPS extension on the NPS.
- If the authentication is successful, the NPS sends a RADIUS Access-Accept message to the VPN or endpoint server.
- The user is granted access to the VPN or endpoint server, and an encrypted tunnel to the internal network is established.
Configuring MFA for VPNs and RADIUS-supporting endpoints
Firstly, you need to decide which MFA mode you wish to use to configure VPN MFA. You can select either VPN Client Verification or SecureLink Email Verification, depending on the authenticators and type of MFA prompts you want to use:
- VPN Client Verification
- Select VPN Client Verification to present users with MFA prompts directly from the VPN client during the login process.
- If your VPN supports the RADIUS challenge prompts, then ADSelfService Plus authenticators like TOTP Authentication, Microsoft Authenticator, YubiKey Authenticator, Zoho OneAuth TOTP, and one-way authenticators like Push Notification Authentication or Biometric Authentication can be selected for VPN MFA.
- If your VPN does not support RADIUS challenge prompts, one-way authenticators like Push Notification Authentication or Biometric Authentication can be selected for VPN MFA.
- SecureLink Email Verification
- Select SecureLink Email Verification to secure VPNs using any authenticator supported by ADSelfService Plus, including authenticators that are not supported by the VPN client, such as FIDO2 Passkeys or Smart Card Authentication.
- When this method is selected, the user will receive a verification link in their mailbox that they need to click to verify their identity.
Note: RADIUS challenge-response prompts are not supported by a few VPN and RADIUS-supporting endpoint providers like Cisco Meraki, Microsoft Routing and Remote Access Service, and the Microsoft Remote Desktop Gateway service. To secure these VPNs and endpoints, you can use either one-way authenticators like Push Notification Authentication and Biometric Authentication or opt to use SecureLink Email Verification.
This mode is compatible with all RADIUS-supporting endpoints regardless of their support for RADIUS challenge-response prompts.
If you are unsure if your VPN client supports RADIUS challenge-response prompts, consult the documentation from your VPN provider or contact the provider's support team for confirmation.
Configuration steps
Prerequisites
- You must have the Professional edition of ADSelfService Plus with Endpoint MFA.
- Your VPN or endpoint server must be configured to use RADIUS authentication.
- For the RADIUS server, you must have a Windows server (Windows Server 2008 R2 and above) with the NPS role enabled.
- You must enable HTTPS in ADSelfService Plus under Admin > Product Settings > Connection.
Note: If you are using an untrusted certificate in ADSelfService Plus to enable HTTPS, you must disable the Restrict User Access when there is an Invalid SSL Certificate option under Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del) > GINA/Mac/Linux Customization > Advanced.
- In AD, set users’ Network Access Permission to Control access through NPS Network Policy under their Dial-in properties.
- In ADSelfServicePlus, the access URL you configure under Admin > Product Settings > Connection > Configure Access URL is used by the NPS extension to communicate with the ADSelfService Plus server. Make sure you update the access URL before installing the NPS extension.
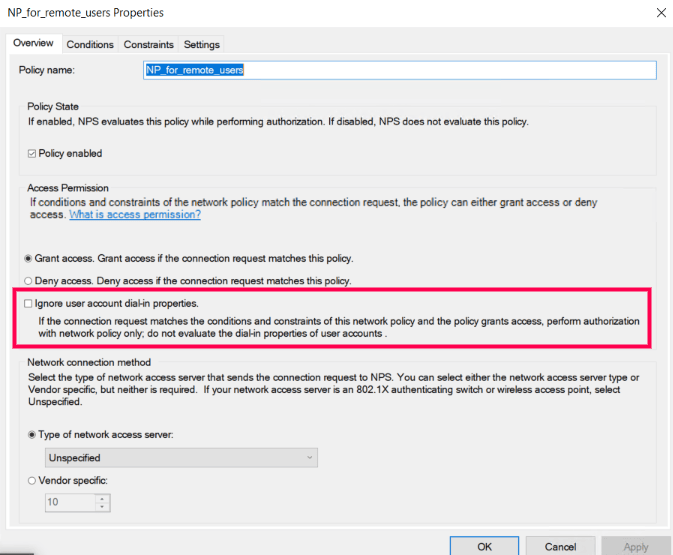
- In the Windows NPS server, where the NPS extension is going to be installed:
- set the Authentication settings of the Connection Request Policy to Authenticate requests on this sever.
- Leave the Ignore user account dial-in properties checkbox under the Overview section of the Network Policy unchecked.
Step 1: Enable the required authenticators
- Log in to ADSelfService Plus as an admin.
- Go to Configuration > Self-Service > Multi-factor Authentication > Authenticators Setup.
- Enable the authenticators that are compatible with the MFA mode decided upon before starting the configuration process.
Authenticators compatible with VPN Client Verification
These authenticators are applicable by default for all the endpoints providing RADIUS authentication. If you will be choosing this mode, you can select either one-way authenticators or challenge-based authenticators.
- One-way authenticators
- Push notification authentication
- Biometric Authentication
Note:
When you enable Push Notification Authentication or Biometric Authentication, make sure the ADSelfService Plus server is reachable by the users through the internet from their mobile devices.
The RADIUS authentication timeout should be set to at least 60 seconds in the VPN server's RADIUS authentication configuration settings. Failing to configure this setting could result in the default timeout (often as low as five seconds) being applied, which may be insufficient for users to complete MFA, potentially causing authentication failures.
- Challenge-based authenticators
- TOTP Authentication
- Google Authenticator
- Microsoft Authenticator
- YubiKey Authenticator (hardware key OTP authentication)
- SMS Verification
- Email Verification
- Zoho OneAuth TOTP
Challenge-based authenticators are applicable only when:
- PAP is configured for the RADIUS authentication method.
- The RADIUS client (the VPN or endpoint server) supports challenge-response prompts; that is, it has a way of prompting the user for a challenge (a verification code) and sending back the entered challenge.
Note:
When challenge-based authenticators are used, the RADIUS attributes that are configured in the network policy won't be forwarded to the RADIUS client (the VPN or endpoint server). As a result, the VPN client might have more access than you want it to have, less access, or no access. To address this, you can use the
Send additional attributes as a response to the VPN server after successful MFA option under
Advanced settings to send the RADIUS attributes to the VPN server from ADSelfService Plus.
Authenticators compatible with SecureLink Email Verification
If you selected SecureLink Email Verification, you can secure your VPN using any authenticator supported by ADSelfService Plus. You can find the list of authenticators here. Click the respective links to learn how to enable these authentication methods.
Note: Avoid using RADIUS Authentication for VPN logins via SecureLink Email Verification if your RADIUS server is also the server on which ADSelfService Plus' NPS extension for VPN authentication has been installed.
Learn more.
The RADIUS authentication timeout should be set to at least 10 minutes in the VPN server's RADIUS authentication configuration settings when using SecureLink Email Verification. Failing to configure this setting could result in the default timeout (often as low as five seconds) being applied, which may be insufficient for users to complete MFA, potentially causing authentication failures.
Step 2: Enable MFA for VPN logins in ADSelfService Plus
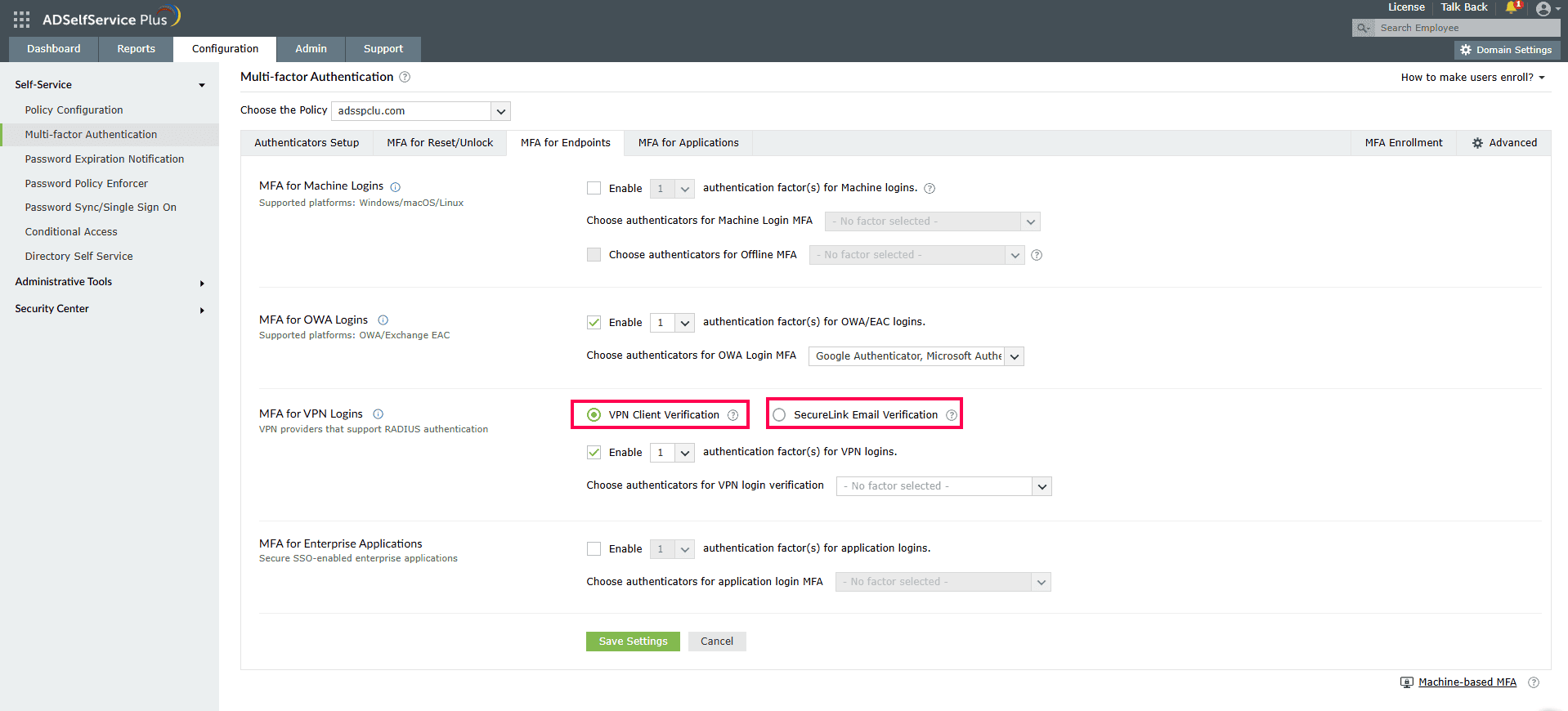
- Go to MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This policy determines the users for whom MFA for VPN and endpoint logins are enabled. To learn more about creating an OU- or group-based policy, click here.
- In the MFA for VPN Logins section, select VPN Client Verification or SecureLink Email Verification, depending on the MFA mode decided upon previously.
- Click the check box next to Select the authenticators required.
- Choose the number of authentication factors to be enforced.
- Select the authentication methods to be used. The authentication methods listed can also be rearranged by dragging and dropping them in the necessary positions.
- Click Save Settings.
Advanced settings
Refer to the advanced settings help document to send additional attributes to the VPN provider, configure the VPN MFA session limit, and enable the option to skip MFA if ADSelfService Plus is unavailable or the user is not enrolled.
You can send additional attributes to the VPN server after successful MFA to determine the level of access each user should have or to serve other purposes. Please refer to the documentation given by your VPN provider for the full list of attributes you can utilize. A list of the most frequently used attributes for the top VPN vendors in the market is given below.
| Vendor |
Attribute type |
Vendor ID |
Attribute number |
Format |
Attribute name |
Attribute Description |
| Fortinet |
Vendor-specific |
12356 |
1 |
String |
Fortinet-Group-Name |
Fortinet performs group-based authorization restriction using this attribute |
| Palo Alto Networks |
Vendor-specific |
25461 |
5 |
String |
PaloAlto-User-Group |
Palo Alto Networks matches the group information to the groups specified in the allowlist of the authentication profile |
| Cisco ASA AnyConnect |
Vendor-specific |
3076 |
25 |
String |
Group-lock |
Cisco uses this attribute to lock access based on the group identity |
| SonicWall |
Vendor-specific |
8741 |
3 |
String |
SonicWall-User-Group |
SonicWall uses this attribute to determine the group the user belongs to |
| WatchGuard |
Standard |
N/A |
11 |
String |
FilterID |
The FilterID attribute is used to identify the user's RADIUS ACL |
| Check Point |
Vendor-specific |
2620 |
229 |
String |
CP-Gaia-User-Role |
Check Point uses this attribute to grant permissions to specific users |
| Citrix |
Vendor-specific |
3845 |
16 |
String |
Citrix-Group-Names |
Citrix uses this RADIUS group extraction method to enable authorization |
Step 3: Install the NPS extension
- Go to MFA for Endpoints.
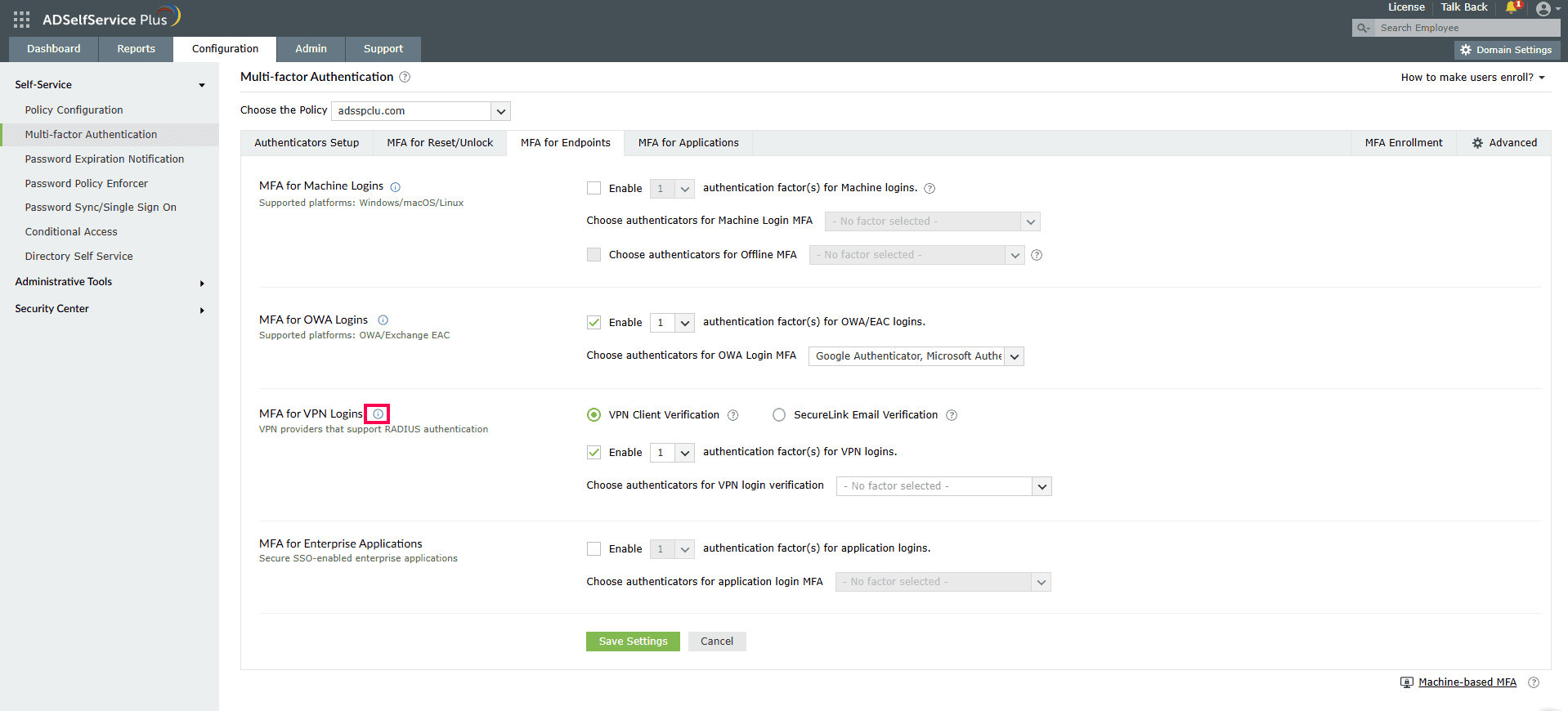
- Click the tooltip icon next to MFA for VPN Logins to display the architecture diagram and download the NPS extension using the link provided in the banner.
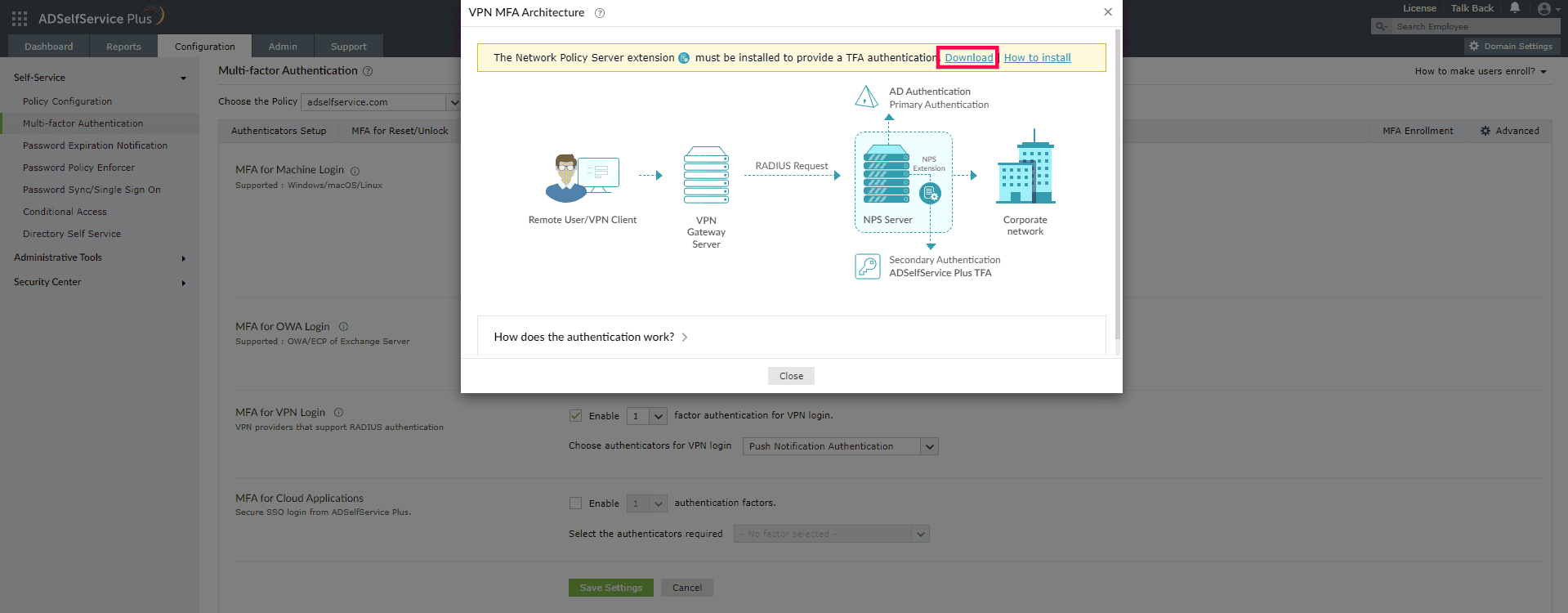
- Copy the extension file (ADSSPNPSExtension.zip) to the Windows server that you have configured as the RADIUS server. Extract the ZIP file’s content and save it in a secure location.
- Open Windows PowerShell as an administrator and navigate to the folder where the extension file's content is located.
- Execute the following command:
PS C:\> .\setupNpsExtension.ps1 Install
Note: If the NPS extension plug-in has to be uninstalled or updated to a newer version, enter Uninstall or Updated, respectively, instead of Install.
- After installation, you will be prompted to restart the NPS Windows service. Proceed with the restart.
Customizing the configuration of MFA for VPNs and RADIUS-supporting endpoints
You can customize the MFA configuration based on your organizational requirements.
To do so:
- Open Registry Editor (type regedit in the Run dialog box).
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\ZOHO Corp\ADSelfService Plus NPS Extension.
Note:
Make a backup of the registry key before editing it. Only the built-in administrator group on the computer has the privilege to edit this key.
- You can customize the properties mentioned below according to your organizational requirements:
- ServerName: Mention the hostname or IP address of the ADSelfService Plus web server.
- ServerPortNo: Mention the TCP port number for the ADSelfService Plus web server.
- ServerContextPath: Mention the web server context path (if configured).
- MfaStatus: This can be set to true or false depending on whether you need MFA to be enforced or not.
- ServerSSLValidation: This can be set to true or false. If set to true, it verifies the SSL certificate and hostname when establishing an HTTPS connection from the NPS extension to the ADSelfService Plus server. It is recommended that the property always be set to true for security reasons.
- BypassMFAOnConnectionError (optional): This property can be set to true or false depending on whether MFA can be bypassed if any connection issue is present during authentication.
- CRPolicies (optional): This property can be used to enforce MFA only for users who fall under these connection request policies. Enter the connection request policies' names, and if more than one policy has to be mentioned, separate the policies' names with semicolons (;).
- NetworkPolicies (optional): This property can be used to enforce MFA only for users who fall under these network policies. Enter the network policies' names, and if more than one policy has to be mentioned, separate the policies' names with semicolons (;).
Note: When both CRPolicies and NetworkPolicies are configured, an authentication request is considered for MFA only if both the CRPolicies and NetworkPolicies of the RADIUS request match the ones configured. If the policies are not configured, MFA is enforced for all the successful RADIUS requests sent to the NPS.
- LogLevel (optional): This property can be used to determine the intricacy of the logged information on the feature's functioning. The property is set to Normal by default and can be changed to Debug to additionally log details that aid with debugging. It is recommended that the property be set to Normal.
- UserIPAttribute (optional): This property's value is a RADIUS request attribute, which can be modified to receive the user's IP address and send it to ADSelfService Plus for conditional access.
The value to be set as the UserIPAttribute property varies with each VPN provider. Please refer to the documentation provided by your VPN provider for the RADIUS attribute value via which the user's IP address is sent.
This attribute can be either standard or vendor-specific.
- If it is a standard attribute, you can set the UserIPAttribute property to the attribute number alone.
- If it is a vendor-specific attribute, you need to mention the vendor ID followed by the vendor-assigned attribute number—separated by a comma—as the UserIPAttribute value.
- Examples using well-known vendors are given in the table below:
| Vendor |
Attribute Type |
Attribute Name |
Vendor ID |
Attribute Number |
UserIPAttribute value |
| Juniper Networks |
Standard |
calling-station-id |
- |
31 |
31 |
| Palo Alto Networks |
Vendor-Specific |
client-source-ip |
25461 |
7 |
25461,7 |
- Click OK.




